Enterprise Security Solution – Firewall, VPN & SBC (Session Border Controller)
Data security is very critical for any business today because that is one way to make one’s business more effective. Business’s data is the lifeline of any business, hence it is imperative to make sure Enterprises can do their job without security threat to their data.
Here are few of the most common security threats organizations face in today’s world:
- External hacking attempts that include phishing, social engineering and IoT device hacking.
- Internal security incidents that include vandalism, property thefts and data pilferage.
- Accidental employee breaches including lackadaisical security policies, insecure networks and outdated security mechanisms.
- Third party risks are typical in organizations that use third party vendors. If these third party vendors do not adhere to the organization strictures laid out they may be compromising on the security.
Enterprise security involves the various technologies, tactics, and processes used to protect digital assets against unauthorized use, abuse or infilterations by threat actors. Enterprise security systems also cover the people and policies that organizations use to secure their network infrastructure, including assets such as devices and various terminal equipment.
Having an effective and well maintained enterprise security program is a must in today’s world that is striped with veiled and unveiled threats of all kinds. Bad actors continually scan the internet looking for vulnerable soft targets. Hence, an effective enterprise security program is crucial to building a defensive posture that makes the bar high enough that those with malicious intent are forced to shift focus to softer targets.
How is *astTECS helping Enterprises counter such threats?
*astTECS has developed various solutions that work in tandem with the product line they offer for voice, data and video communications and help mitigate threats posed by the above vulnerabilities. *astTECS has launched products like astFirewall, Virtual Private Network (ast VPN) solutions and Sessions Border Controllers (ast SBC) and these solutions have found homes with a number of customers globally.
What is a Firewall?
A firewall is a network security device that monitors incoming and outgoing network traffic and decides whether to allow or block specific traffic based on a defined set of security rules.
Firewalls have been a first line of defense in network security for over 25 years. They establish a barrier between secured and controlled internal networks that can be trusted and untrusted outside networks, such as the Internet.
A firewall can be either hardware or software, or both.
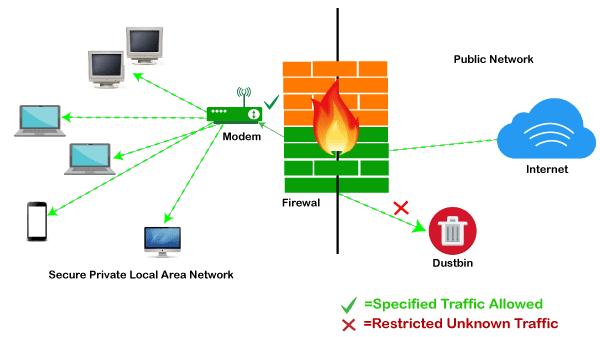
* ast Firewall:
*ast Firewall is an open-source, easy-to-use and easy-to-build hardened BSD based firewall and routing platform. *ast Firewall is very feature rich and has much more to offer than its competitors. *ast Firewall can filter traffic on source, destination and protocol as well as port on number (TCP/UDP), Operating System Fingerprinting (OSFP). Advanced passive OS fingerprinting technology can be used to allow or block traffic based by the Operating System initiating the connection. *ast Firewall’s features offered can be configured through responsive user interface. The user interfaces support multi-language with in-built help to get you started quickly.
*ast Firewall offers a wide range of VPN technologies ranging from modern SSL VPN’s to well known Ipsec as well as older (now considered insecure) legacy options such as L2TP and PPTP. It provide users with secure, seamless remote access to corporate networks and resources when traveling or working remotely from any devices – smartphones, tablets, PCs and laptops with two factor authentication.
*astVPN and its variants:
A virtual private network secures public network connections and in doing so it extends the private network into the public network such as internet. With a VPN you can create large secure networks that can act as one private network.
*astVPN supports VPN connections for branch offices as well as remote users. Creating a single secured private network with multiple branch offices connecting to a single site can easily be setup from within the graphical user interface. For remote users, certificates can be created and revoked and a simple to use export utility makes the client configuration a breeze.
*astVPN supports the following most widely used variants:
- Open VPN: A powerful SSL VPN solution supporting a wide range of client operating systems including mobile (Android / iOS).
- IPSec VPN: It connects site to site in an organization together and allows secure communications between the sites. The connectivity is allowed with any device supporting standard IPsec.
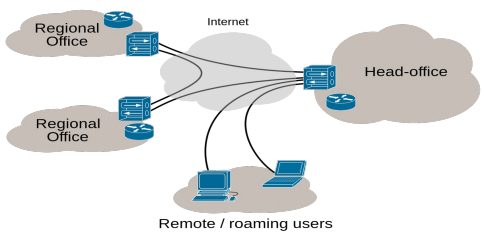
Fig : Internet VPN
Session Border Controller:
What is SBC?
A Session Border Controller (SBC) is a network function which secures voice over IP (VoIP) infrastructures while providing interworking between incompatible signaling messages and media flows (sessions) from end devices or application servers. SBCs are employed in Enterprise infrastructures or any carrier network delivering commercial residential, business, fixed-line or mobile VoIP services. They are typically deployed at both the network edge and at carrier interconnects, the demarcation points (borders) between their users and other service providers.
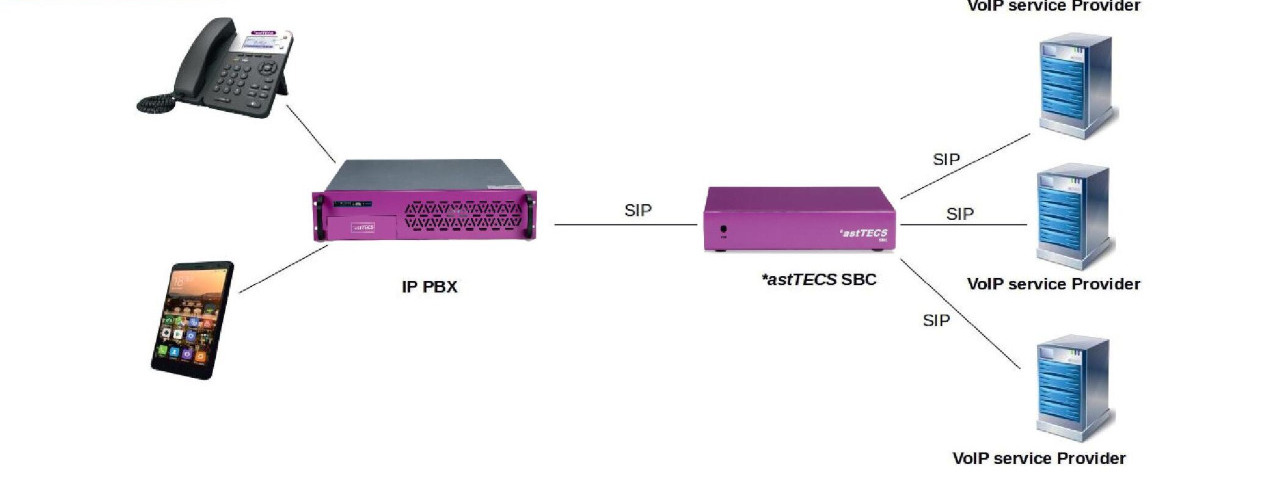
*astSBC connects any IP PBX to any Internet-based, next-generation network. With integrated ESBC functions for any signalling adaptations, *astSBC is an ideal demarcation point for the interface between enterprise premises and wide area networks. The two Ethernet interfaces allow a physical independent connection to LAN and WAN.
The optional TDM alternative supporting two E1 interfaces allows a connection to the traditional TDM equipment. *astSBC has multiple integrated features which allows an easy management and provides additional security functions
Finally, demarcation between Firewall, VPN and SBC:
Firewalls prevent malicious attacks by allowing you to set your security preferences and what you allow to enter your computer. A Firewall is a specially programmed router that sits between a site and the rest of the network.
VPNs can only protect the data from where the network connection was created or in the VPN tunnel. They do not protect your computer. A VPN is also an example of providing a controlled connectivity (imagine a secure pipe) over a public network such as the Internet. VPNs protect the connection between points A and B, but not the applications on either side.
SBCs, on the other hand, are application-aware and will only let legitimate SIP-based traffic pass through. It is a network element deployed to protect SIP based voice over Internet Protocol networks while providing interworking between incompatible signaling messages and sessions from end devices or application servers.
Let us know in the comments which security solution are you using for your organisation Or Contact us to speak with our experts on Enterprise Security Solution requirement.




Leave A Comment